Identify → Assess → Comply

GRC Consulting Services
✓ Compliance Management
✓ Audit and Assessment
✓ Cybersecurity Strategy and Planning
✓ Standards and Frameworks
✓ Governance and Risk Management
✓ Data Governance and Privacy
Cyber Security Assessment Offerings
✓ Technical Analysis & Security Review
✓ Next Gen Platform Review
✓ Application Security Review
✓ Network Security Architecture Review
✓ Penetration Testing
✓ Dedicated Red & Blue Teams
✓ Vulnerability Assessment & Penetration Testing (VAPT Services)
✓ Intrusion Protection & Intrusion Detection

Business Outcomes and Deliverables
✓ Help Customers Develop Security Services Portfolio Security As A Service
✓ Help Customers Align Their Cybersecurity Practices Against International Standards
✓ Help Customers Comply Against International Standards
✓ Help Customers Improve Their Cybersecurity Posture
Compliance Framework Assessment & Implementation Services
CPS/CPG 234
• CPS/CPG 234 Assessment and Preparedness
• CPS/CPG 234 Roadmap
• CPS/CPG 234 Implementation
ISO27K
• ISO27001:2013 Audit and Assessments
• ISO27001:2013 Implementation and Certification
PCI DSS
• PCI DSS v3.2.1 Audit (QSA)
• PCI DSS v3.2.1 Controls Implementation
NIST CSF
• NIST CSF Assessments and
• NIST CSF Strategy and Roadmap
• NIST CSF Framework Implementation
GDPR
• GDPR Assessment and Preparedness
• GDPR Implementation
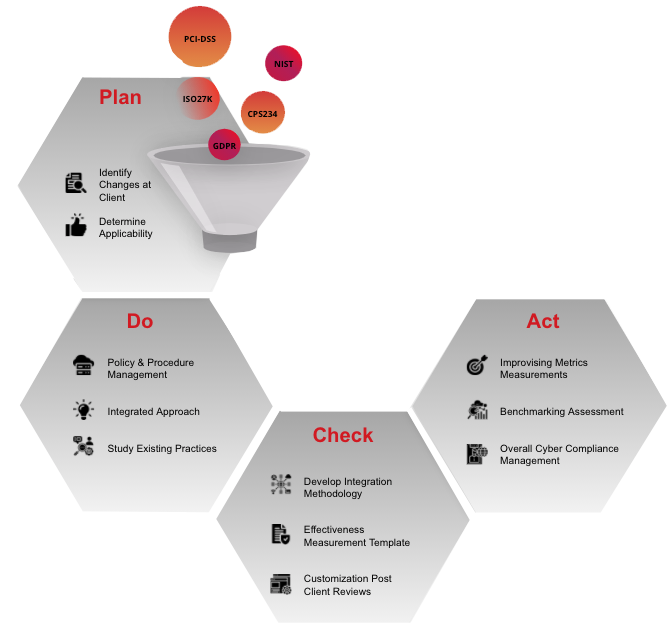
Consulting & Advisory Services General Approach
The Plan-Do-Check-Act process works in tandem.
PLAN
• Identify the risks
• Devise the strategy and roadmap
• Put a plan together to mitigate the risks
DO
• Our Executive Consultants work with your team to implement the agreed
actions
CHECK
• Internal or external assurance activity to help identify any gaps in the controls implementation
ACT
•Management and respective teams agree and initiate the next set of activities to close the gaps identified in the Check phase.
The process will continue in an ongoing manner as part of Continual Improvement process to manage and mitigate the cybersecurity risks faced by the organisation.
BOOK A CONSULTATION TODAY!
Have questions about our technology or services? We want to talk to you.
BOOK NOW